Lazarus Group’s Money Laundering After Bybit Hack
How the Lazarus Group laundered funds after the $1.5 billion Bybit hack, using complex strategies like token swaps, DEXs, and cross-chain bridges.
Lazarus Group’s Money Laundering After Bybit Hack
The Lazarus Group, a notorious North Korean state-sponsored hacking collective, has been implicated in numerous high-profile cybercrimes, including the audacious $1.5 billion Bybit hack. Following such a massive cryptocurrency theft, the subsequent money laundering operation becomes a critical component for converting illicit gains into usable funds. This article delves into the intricate strategies employed by the Lazarus Group to obfuscate the origins of stolen cryptocurrency, focusing on their use of token swaps, decentralized exchanges (DEXs), cross-chain bridges, and other sophisticated techniques. Understanding these methods is paramount for cybersecurity professionals, cryptocurrency investors, and anyone interested in the evolving landscape of cybercrime and **cryptocurrency security**.
The group’s techniques are constantly evolving, making them a persistent threat to the global financial system. They are known for their ability to adapt to new technologies and exploit vulnerabilities in emerging **cryptocurrency** platforms. This article aims to shed light on the specific tactics used in the Bybit case and provide a broader understanding of how the **Lazarus Group** operates in the realm of **money laundering**. The complexities of **blockchain analysis** in tracking these illicit funds will also be explored, highlighting the challenges faced by law enforcement agencies in their pursuit of cybercriminals.
We will examine how the **Lazarus Group** leverages various cryptocurrency platforms to break the chain of custody and create a complex web of transactions that are difficult to trace. This includes the use of mixers and tumblers to further obfuscate the origins of the funds, as well as the strategic deployment of **token swaps** and **DEX** platforms to convert stolen assets into different cryptocurrencies. The use of **cross-chain bridges** to move funds between different blockchains adds another layer of complexity to the investigation, making it even more challenging to track the flow of illicit funds.
Finally, this article will underscore the importance of proactive measures to mitigate the risk of future attacks and enhance **cryptocurrency security**. This includes the implementation of robust security protocols, enhanced monitoring and surveillance capabilities, and increased collaboration between industry stakeholders and law enforcement agencies. By understanding the tactics used by the **Lazarus Group**, we can better protect ourselves from becoming victims of **cybercrime** and help prevent future **crypto heist** incidents.
INSIDE THE LAZARUS GROUP MONEY LAUNDERING STRATEGY
The Lazarus Group’s **money laundering** strategy following the **Bybit hack** is characterized by its sophistication and complexity. It’s not simply a matter of transferring funds from one account to another. Instead, the group employs a multi-layered approach designed to break the chain of custody and obfuscate the origin of the stolen cryptocurrency. This strategy typically involves several key steps:
۱. **Initial Obfuscation:** The first step involves moving the stolen funds through a series of intermediary wallets. These wallets, often newly created and controlled by the attackers, serve as a buffer to distance the funds from the initial hack.
۲. **Mixers and Tumblers:** Cryptocurrency mixers and tumblers are services that combine multiple cryptocurrency transactions to obscure the links between the sender and the receiver. The Lazarus Group often utilizes these services to further complicate the tracing of funds.
۳. **Token Swaps:** Converting the stolen cryptocurrency into other cryptocurrencies using **token swaps** is a common tactic. This is often done on decentralized exchanges (DEXs) to avoid the Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations of centralized exchanges.
۴. **Decentralized Exchanges (DEXs):** **DEX** platforms offer a permissionless and often anonymous trading environment, making them ideal for laundering illicit funds. The **Lazarus Group** frequently uses DEXs to swap stolen cryptocurrency for other assets, further obscuring the trail.
۵. **Cross-Chain Bridges:** **Cross-chain bridges** allow for the transfer of cryptocurrency assets between different blockchains. This allows the **Lazarus Group** to move funds from one blockchain to another, making it more difficult to track the flow of funds across different networks.
۶. **Cash-Out Points:** The final stage involves converting the laundered cryptocurrency into fiat currency or other assets that can be used in the real world. This can be achieved through various means, including over-the-counter (OTC) trading, the purchase of goods and services, or the use of prepaid debit cards.
This complex process requires a deep understanding of cryptocurrency infrastructure, **blockchain analysis**, and the regulatory landscape. The Lazarus Group’s ability to execute these operations successfully highlights their sophistication and the challenges faced by law enforcement agencies in combating **cybercrime** and recovering stolen assets.
Leveraging Decentralized Exchanges (DEXs) and Token Swaps
Decentralized Exchanges (DEXs) have become a cornerstone of the **Lazarus Group’s** money laundering operations. Unlike centralized exchanges, DEXs operate without a central authority, allowing users to trade cryptocurrencies directly from their wallets without the need for an intermediary. This lack of centralized control makes DEXs attractive for laundering illicit funds, as they often have weaker KYC/AML requirements.
**Token swaps**, which involve exchanging one cryptocurrency for another, are frequently conducted on DEXs to obscure the origin of stolen funds. The Lazarus Group might, for example, swap stolen Bitcoin for Ether, and then Ether for a privacy-focused cryptocurrency like Monero. This process creates a complex web of transactions that are difficult to trace back to the original theft.
Furthermore, DEXs often utilize automated market makers (AMMs), which rely on liquidity pools to facilitate trading. This means that large volumes of cryptocurrency can be swapped with minimal slippage, making it easier for the **Lazarus Group** to launder substantial amounts of money without drawing attention.
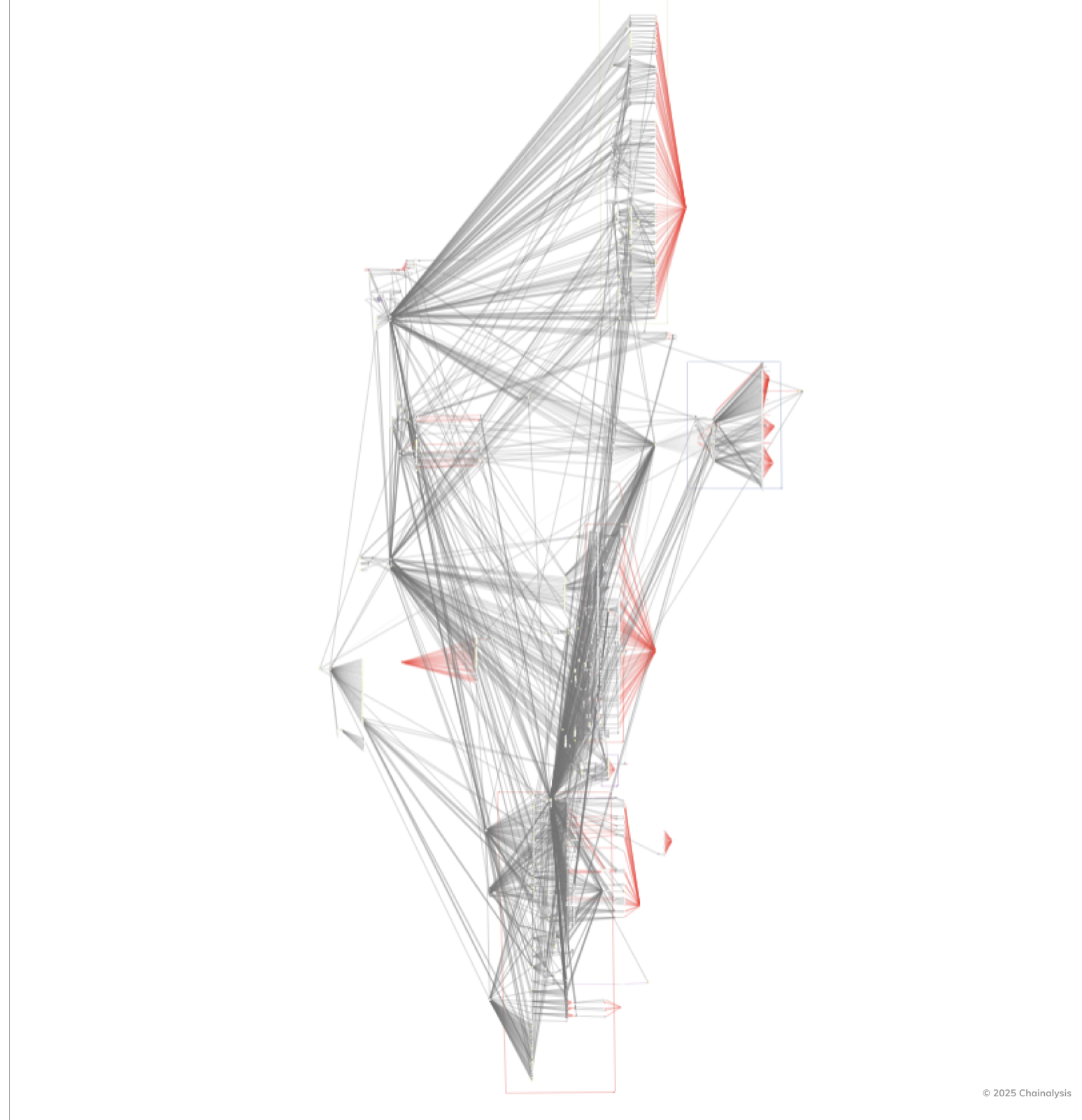
The Role of Cross-Chain Bridges in Obfuscation
**Cross-chain bridges** have emerged as another powerful tool in the **Lazarus Group’s** arsenal. These bridges enable the transfer of cryptocurrency assets between different blockchains, allowing for the movement of funds from, say, the Ethereum network to the Binance Smart Chain or Solana. This capability introduces another layer of complexity to the tracking of illicit funds.
By utilizing **cross-chain bridges**, the Lazarus Group can break the direct link between transactions on a single blockchain. This makes it more difficult for **blockchain analysis** tools to trace the flow of funds, as the transaction history is fragmented across multiple networks. The group can also exploit vulnerabilities in cross-chain bridges themselves, potentially creating new avenues for theft and money laundering.
For example, if the group steals Ethereum, they might use a bridge to convert it into Wrapped Bitcoin (WBTC) on the Bitcoin blockchain. This WBTC can then be further laundered through Bitcoin-specific mixing services or used to purchase goods and services that accept Bitcoin.
Challenges in Blockchain Analysis and Law Enforcement
Tracking the **Lazarus Group’s money laundering** activities poses significant challenges for **blockchain analysis** and law enforcement agencies. The sophisticated techniques employed by the group, including the use of mixers, DEXs, and **cross-chain bridges**, make it extremely difficult to trace the flow of funds and identify the individuals or entities involved.
Furthermore, the decentralized nature of cryptocurrency and the global reach of the internet complicate the investigation process. Law enforcement agencies must collaborate across international borders to gather evidence and pursue legal action against the perpetrators. This requires overcoming legal and regulatory differences, as well as navigating the complexities of international extradition treaties.
Another challenge is the constantly evolving nature of **cryptocurrency** technology and the emergence of new money laundering techniques. Law enforcement agencies must stay ahead of the curve by developing new tools and strategies for tracking illicit funds and combating **cybercrime**. This requires investing in research and development, as well as fostering collaboration between law enforcement, cybersecurity experts, and the **cryptocurrency** industry. Understanding concepts like “What is Blockchain?” can be crucial in this effort.
Here’s a comparison table illustrating the challenges in tracing funds through different methods employed by the Lazarus Group:
| Method | Difficulty Level | Impact on Traceability |
|———————–|——————|————————–|
| Direct Transfers | Low | Easily Traceable |
| Cryptocurrency Mixers | Medium | Obscures Direct Links |
| DEXs & Token Swaps | High | Complicates Tracing |
| Cross-Chain Bridges | Very High | Fragments Transaction History |
Mitigating Future Risks and Enhancing Cryptocurrency Security
To combat the threat posed by the **Lazarus Group** and other cybercriminals, it is essential to implement proactive measures to mitigate future risks and enhance **cryptocurrency security**. This requires a multi-faceted approach that involves collaboration between industry stakeholders, law enforcement agencies, and regulatory bodies.
Some key strategies for mitigating future risks include:
* **Strengthening KYC/AML Regulations:** Enhancing KYC/AML regulations on centralized **cryptocurrency** exchanges can help prevent the laundering of illicit funds. This includes implementing stricter identity verification procedures, monitoring transactions for suspicious activity, and reporting suspicious transactions to law enforcement agencies. Platforms for buying **Tether**, for instance, should have robust security measures in place.
* **Improving Blockchain Analysis Tools:** Developing more sophisticated **blockchain analysis** tools can help law enforcement agencies track the flow of illicit funds and identify the individuals or entities involved in **money laundering**. This includes tools that can analyze transactions across multiple blockchains and identify patterns of suspicious activity.
* **Enhancing Cybersecurity Measures:** Implementing robust cybersecurity measures can help prevent future **crypto heist** incidents. This includes using strong passwords, enabling two-factor authentication, regularly updating software, and being wary of phishing scams. Choosing the **Best Crypto Wallets** is also a critical step.
* **Promoting Education and Awareness:** Educating individuals and businesses about the risks of **cybercrime** and the importance of **cryptocurrency security** can help prevent future attacks. This includes providing training on how to identify phishing scams, how to protect cryptocurrency wallets, and how to report suspicious activity.
* **Fostering Collaboration:** Fostering collaboration between industry stakeholders, law enforcement agencies, and regulatory bodies is essential for combating **cybercrime**. This includes sharing information about emerging threats, coordinating investigations, and developing joint strategies for preventing and responding to attacks. Considering what **Cryptocurrency** truly entails is also important for a well-rounded understanding.
By implementing these strategies, we can create a more secure and resilient **cryptocurrency** ecosystem, making it more difficult for the **Lazarus Group** and other cybercriminals to profit from their illicit activities.
In conclusion, the **Lazarus Group’s money laundering** operation following the **Bybit hack** serves as a stark reminder of the evolving sophistication of **cybercrime** and the challenges faced in combating it. Their use of **token swaps**, **DEXs**, and **cross-chain bridges** highlights the need for continuous innovation in **blockchain analysis** and enhanced security measures across the cryptocurrency landscape. By understanding the tactics employed by these cybercriminals, stakeholders can proactively implement mitigation strategies to protect against future attacks. The fight against cryptocurrency crime is an ongoing battle, demanding vigilance, collaboration, and a commitment to staying one step ahead of malicious actors.
Are you concerned about the security of your cryptocurrency investments? Learn how to protect your digital assets today! Contact us for a consultation and discover the best practices for securing your cryptocurrency holdings.

Comments are closed.